CHAPTER FOUR:
METHODOLOGY
Overview
This chapter details the methodology used in this research study. The research design section provides more details about the methodology used to analyze the interview data. It emphasizes the method used to collect data, which emphasized interviewing individuals until data novelty saturation. The data collection section describes how the interview participants were selected and why. Then, an explanation of the methodology of how the study invitation was solicited as well as IRB approval, is provided. The last section in this chapter delineates the coding methodology and coding results.
Research Design
Interview Until Data Novelty Saturation
To understand the risk perceptions of people pertaining to their digital identity, the first set of questions were geared towards discovering digital identity and online personal data. This discovery includes information on what data people share online, as well as their knowledge about their online personal data and online interactions. The second section discusses current behavior online, while the last set of questions addresses future and unmet needs. The interviews were conducted until data novelty was reached. Data novelty was determined to be saturatedwhen the interviews started generating repetitive information. The data novelty was reached at approximately 20 interviews.
Process Followed
Using an inductive, interpretive approach, the interview transcripts were first analyzed using a “top-down” approach, where the transcripts were reviewed and analyzed for overall context. The second iteration was conducted using a “bottom-up” approach to try to determine the core findings and overarching themes to help answer the research question (Neck, 2015).
In the thematic analysis that supports this qualitative research, the process followed started with the literature review and the group of preliminary themes found in the academic and industry-focused literature. The next step involved composing a coherent qualitative questionnaire driven by the findings in the literature and exploring some of the causes and gaps of what was found in the literature. The goal was to inquire into the research population of people aged 55 to 75years-old, with no technical IT background to determine their awareness of the risks pertaining to their digital identity. The coding technique helped to uncover the scheme of the themes that this exploratory research sought at its essence.
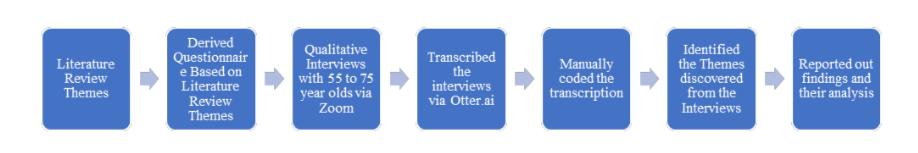 Figure 6. Methodology Process Followed Thematic Analysis.
Figure 6. Methodology Process Followed Thematic Analysis.
Thematic Analysis
Thematic analysis (TA) is a concept recognized as qualitative research that falls between grounded theory and social phenomenology (Braun & Clarke, 2006). Four authors highlight the use of TA: Boyatzis, Clarke, Braun, and Fereday. Boyatzis was one of the first researchers to document the mechanics of going through the analysis in his book Transforming Qualitative Information (Boyatzis, 1998; Braun & Clarke, 2006; Clarke & Braun, 2018; Fereday & MuirCochrane, 2006). As a result of performing a TA over a set of qualitative interview transcripts, common themes were discovered and portrayed in a group of findings that tell a story that is compelling and answers the research question being investigated.
There have been different interpretations, variations, and adjustments of TA throughout the years. Just like any good framework, it is adapted to the investigator’s use case and purpose of research. In his book Transforming Qualitative Information, Boyatzis (1998) described an inductive approach, which aligns with the grounded theory methodology described in Saldaña (2016). The inductive or grounded theory analysis approach aims to develop a theory as a result of the analysis of whether a deductive approach tends to go through the qualitative analysis with theory and hypothesis in mind and work to validate the theory (Hyde, 2000).
Considering this study falls in the category of exploratory research, an inductive approach is the more appropriate method of analysis. The goal of this analysis is to illustrate findings and themes from the qualitative interviews that led to the use of the underlying framework as described by Braun and Clarke in their six-step approach (2006). The six steps are:
- Familiarize yourself with your data
- Generate initial codes
- Search for the themes
- Review the themes
- Define and name the themes
- Produce the report
The adaptation of the thematic analysis illustrated in the diagram below reflects the adaptation of the thematic analysis methodology to the coding, illustration, and analysis of the findings in this research study. The Adapted Thematic Analysis (ATA) approach allows the coder to utilize the inductive approach used in grounded theory analysis with the blend of the three steps of open coding, axial coding, and selective coding approach as outlined by Corbin and Strauss (2014). In this study, the three steps used in grounded theory, as well as the six steps used by Braun and Clarke in TA, led to the development of the ATA.
Why the ATA for this Study
The ATA is the most appropriate method for analyzing this research because it provides the simplicity of a structured approach in conducting the coding of the transcripts. This approach is simple enough to understand and fit the thematic analysis steps illustrated by Braun and Clarke in a clear sequence that is easy to use and replicate while limiting ambiguity that may cause confusion and uncertainty to some researchers. The ATA representation framework diagram is represented in the figure below:
 Figure 7. Adapted Thematic Analysis Framework.
Figure 7. Adapted Thematic Analysis Framework.
Data Collection
The data collection process for this study occurred through a series of 15 to 30-minute interviews of individuals who were at least 55 years old. This age range was selected because those within this range tend to be closer to retirement and less computer savvy than the younger generation. The researcher interviewed participants from various professional backgrounds to over a wide range of populations and make the research study sample size as diverse as possible.
The interview questions were formulated in an open-ended qualitative way, with some specific follow up sub-questions, to ensure the individuals understood the questions and answered them adequately. The goal was to gauge their understanding and awareness regarding their online interactions and the associated risks, as well as their awareness of what online personal data they share that constitutes their digital identity footprint.
Interviews started in March 2020 and concluded in May 2020. The interviews were recorded via various software and hardware tools, then loaded into an online transcription service called Otter.ai to be transcribed. The lead researcher went through the transcription as well as the voice-over to verify accuracy. The researcher made the appropriate edits when the software didnot translate accurately. The transcripts were then loaded into a coding template to perform the appropriate coding methodology.
Participant Selection
Participants in the study were solicited in various ways. The lead researcher placed flyers in various public places that attract the targeted population. Flyers were put up in several grocery stores and coffee shops. The researcher also leveraged his social media pages, LinkedIn and Facebook, as well as his personal connections to solicit interview participants. The originallyintended approach was not as effective in recruiting participants. The recruitment of participantswas derailed by the complete worldwide lockdown due to an unpredicted global event. As a result, the researcher transitioned to a referral approach, where a handful of original interviewees recruited served as a link to recruit their friends, colleagues, or family members. Participants were helpful and eager to help, especially during the tough times and the unprecedented event the world was experiencing. Interviews were conducted until novelty in the data was reached (Creswell & Poth, 2018; Saldaña, 2016; Seidman, 2013).
Interview Participants Characteristics
Twenty interview participants were involved in this study. They were from three different countries: 10% from the United Kingdom, 20% from Canada, and 70% from the United States.
From an employment perspective, 35% were retired, 65% were actively working with 25% working in education, and 30% being business owners.
Study Invitation
Every interview participant received an email with the solicitation flyer from Appendix A, the Interview questionnaire from Appendix C, and the IRB consent form from Appendix B. All participants provided verbal consent to participate in the interview, per the IRB protocol guidelines. Interviews were scheduled based on schedule availability and conducted via video conferencing software. The video conferencing software, Zoom, has a recording capability that was used to record the interviews; transcription occurred via a separate third-party software, Otter.ai.
IRB Approval
The Institutional Review Board (IRB) at the University of South Florida gave permission to conduct this study under Study #000341.
Data Analysis
Coding Method
Top-down open coding. In the first phase of the analysis, a top-down approach (Neck, 2015) was used to review all 20 interview transcripts. This first review was used to become familiar with the data; it helped to form an initial idea about the content and cohesiveness of the transcripts (Braun & Clarke, 2006). During this process, the fact that the investigator was also the person writing the analysis and the report helped tremendously. In this open coding section as well, the transcripts were grouped by the topics that helped shape the interview questionnaire, which was the mechanism used to collect the transcripts’ data. This initial set of groupings helped form categories of data points collected to be used in the analysis.
 Figure 8. Transcripts to Open Coding Relationship.
Figure 8. Transcripts to Open Coding Relationship.
Bottom-up axial coding. In the second phase of the analysis, after getting familiar with the data and identifying the grouping as well as the first level of condensed findings, axial coding was performed to generate the initial codes and identify the core finding from the consolidated interviews. These core findings units of analysis contributed to the discovery of the more general overarching themes.
In the third phase, after setting up the initial set of groupings and having the first set of codes produced, the search for common themes began. This phase helped to re-focus the analysis at the broader level of themes and thinking about sorting the different codes into potential themes as well as exploring the option of rearranging the grouping of the codes. This phase focused on the codes generated instead of the initial transcripts
 Figure 9. Open Coding to Axial Coding Relationship.
Figure 9. Open Coding to Axial Coding Relationship.
Illustrate findings by themes or key concepts. In the fourth phase, the second level of coding happened after the initial codes were already identified. In this phase, the first level codes were reorganized and grouped based on the common themes found in the bottom approach. In this phase, a reorganization of the items identified in the axial coding phase occurred.
In the fifth phase, the high-level overarching themes found were refined and named appropriately to help reinforce and answer the research question guiding the study. In the sixth, or last stage, the themes found helped to guide the final analysis and write up of the report. Thisstage helped to tell a compelling story to convince the reader of the merit and the validity of the analysis (Braun & Clarke, 2006).
 Figure 10. Axial Coding to Themes.
Figure 10. Axial Coding to Themes.
Coding Results
Open coding. Open coding is the initial line by line coding process of the interview transcripts. During this process, the first line of groupings was identified by the questions asked in the interview process. It served as a way for the investigator to start thinking about the different groupings.
The first set of groupings and the information coded from each question are displayed in the table below.
Table 2. Open Coding and Groupings
| Grouping | Open coding results from transcripts |
| Time spent connected online (Includes the use of email, messaging apps and surfing the web) | 0 to 4 hours a day: 35% - Moderately Active 4+ hours a day: 65% - Active |
| Online profiles adoption | Online accounts in the last 5-10 years: 20+ Accounts: 13 people or 65% (The highest number being 100+) Less than 20 accounts: 7 people or 35% (The lowest number is 5) Note: People didn't remember all their online accounts from the past 5-10 years, even with the help of tools Email: 100% Social Media(Facebook, Instagram, LinkedIn…): Yes: 13 people - 65% & No: 7 people - 35% Online Banking: Yes: 85% & No: 15% Online Purchases: 100% |
| Digital identity and online personal data composition awareness | All the interview participants think that their online digital identity is comprised of their online personal identifiers like name, address, phone number, birthday, as well as their online behavior and interactions |
| Level of comfort in entering personal information online | - Are hesitant or cautious when entering personal information online - Try to reduce their digital footprint when possible - Accept the risk when convenient and consider it part of their way of life |
| Have been, or knows someone, affected by the loss of online personal data | Yes: 17 - 85% No: 3 - 15% |
| Impact of online interactions risks identified on behavior change | Yes: 3 - 15% No: 17 - 85% |
| Reputational concerns around digital identity compromise | Yes: 11 people or 55% have reputational concerns People that have reputational concerns are mostly customer or student facing in their current jobs or influential in their societies and social groups No: 9 people or 45%, do not have any major concerns or have not thought about it much |
| Financial concerns around digital identity compromise | Yes: 9 people or 45%, have financial concerns (Most of the people that have concerns got affected or someone in their close proximity got affected by a financial hack) No: 11 people or 55% do not have any financial risks concerns (The majority of the interviewees that do not have financial concerns either do not actively bank online or have faith in their financial institutions to take care of their money) |
| Digital identity risks keeping you from fully using the internet | Yes: 4 people - 20% No: 16 people - 80% |
| Companies providing user-friendly information regarding their breaches | Yes: 4 people - 20% (2 people - Helpful, 2 people – Not helpful & Didn't know what to do with info provided) No: 13 people - 65% N/A: 3 people - 15% |
| Familiarity with online privacy rules and regulations | Yes: 17 people - 85% The majority heard of them, very few have encountered instances where they had to research them and are more aware No: 3 People - 15% never heard of them |
| Online companies being transparent with regards to personal information withheld | Yes: 5 people - 25% No: 8 people - 40% Don't Know what to look for: 7 people - 35% |
| Companies need to communicate to gain client trust | - Need to be more transparent with regards to personal information withheld: 2 people - 10% - Doesn't want more details: 2 people - 10% - Doesn't know what to look for: 7 people - 35% - Want more user-friendly information and disclosures: 7 people - 35% - Are interested in transparent details. Use third-party tools to manage online information (LifeLock seems to be popular) 2 people - 10% |
| Actions to keep online identity secure | - Don't know what to do: 4 people 20% - Change password more frequently: 9 people 40% - Research companies before using them online, and only deal with reputable companies - Be more cautious about clicking links from untrusted emails (Phishing) - Minimize online footprint - Take regular training to increase awareness - Only provide information to companies a person solicits - Use a password manager and various other available tools - Clean cookies and history regularly - Limit the use of public Wi-Fi - Monitor financial accounts regularly |
| Awareness of the availability of tools or training to keep digital identity more secure | Yes: 75% No: 25% |
| Had Cybersecurity training | Yes: 80% No: 20% |
| Grouping | Open coding results from transcripts |
| Thoughts about training | Helpful: 7 people - 35% Would like to be trained: 2 people - 10% Needs to be more user-centric and relevant: 9 people - 45% Does not care for it: 2 people - 10% |
| Accounts & password management systems adoption | Paper: 25% Electronic password manager or electronic manual system: 30% None: 45% |
| Ideal solution to keep identity more secure | - Use websites in incognito mode: 1 person - 5% - Mask credit card information: 1 person - 5% - Don't know what to look for: 6 people - 5% - A tool to provide more transparency and control: 7 people - 35% - Digital Identity management tool (Keep track of passwords and websites): 6 people - 30% - A tool to provide what digital identity information out on the internet: 7 people - 35% - A tool to notify if anyone unauthorized used their digital identity: 7 people - 35% - Universal username and password with some way of authentication - A tool to eliminate complexity in accessing online accounts |
| Unmet needs to keep digital identity more secure | More transparency & control: 6 people - 30% No or doesn't know what to look for: 8 people - 40% Would like training and information about options: 6 people - 30% |
Table 3. Open Coding to Axial Coding.
| Open coding | Axial coding (Core findings) |
| Time spent connected online (Includes the use of email, messaging apps and surfing the web) 0 to 4 hours a day: 35% - Moderately Active 4+ hours a day: 65% - Active | Most people between the ages of 55 to 75 are active online |
| Online profiles adoption Online accounts in the last 5-10 years: 20+ Accounts: 13 or 65% (Highest number being 100+) Less than 20 accounts: 7 or 35% (Lowest number is 5) Note: People didn't remember all their online accounts from the past 5-10 years, even with the help of tools Email: 100% Social Media(Facebook, Instagram, LinkedIn…): Yes: 13 - 65% & No: 7 - 35% Online Banking: Yes: 85% & No: 15% Online Purchases: 100% | Most of the population didn't readily know all the online accounts they used in the last 5 to 10 years |
| Digital identity and online personal data composition awareness All the interview participants think that their online digital identity is comprised of their online personal identifiers like name, address, phone number, birthday, as well as their online behavior and interactions | Acknowledged that their Digital Identity encompasses online personal data as well as online interactions, associations, and behavior |
Level of comfort in entering personal information online
| Accept the risk as it is part of life right now, especially when the convenience outweighs the risks |
| Have been or knows someone affected by the loss of online personal data Yes: 17 - 85% No: 3 - 15% | Most people have been or know someone who has been affected by an online data breach |
| Impact of online interactions risks identified on behavior change Yes: 3 - 15% No: 17 - 85% | People's online behavior was not affected by experiencing or knowing about cybersecurity breaches |
| Reputational concerns around digital identity compromise Yes: 11 people or 55% have reputational concerns People that have reputational concerns are mostly customer or student facing in their current jobs or influential in their societies and social groups No: 9 people or 45%, do not have any major concerns or have not thought about it much | Risks about online presence and reputation being compromised mattered to individuals who are socially active, influential or their jobs get affected by a digital identity compromise |
| Open coding | Axial coding (Core findings) |
| Financial concerns around digital identity compromise Yes: 9 people or 45%, have financial concerns (Most of the people that have concerns got affected or someone in their close proximity got affected by a financial hack) No: 11 people or 55% do not have any financial risks concerns (The majority of the interviewees that do not have financial concerns either do not actively bank online or have faith in their financial institutions to take care of their money) | Risks about online banking and financial losses mattered to people who have been directly or indirectly affected by a compromise. People seem to trust their financial institutions to protect them and their money |
| Digital identity risks keeping you from fully using the internet Yes: 4 people - 20% No: 16 people - 80% | Digital identity compromises and cybersecurity risks are not a deterrent for people fully using the internet for their needs |
| Companies providing user-friendly information regarding their breaches Yes: 4 people - 20% (2 people - Helpful, 2 people - Not helpful & Didn't know what to do with info provided) No: 13 people - 65% N/A: 3 people - 15% | In very rare occasions, companies are providing details about online data breaches |
| Familiarity with online privacy rules and regulations Yes: 17 people - 85% The majority heard of them, very few have encountered instances where they had to research them and are more aware No: 3 People - 15% never heard of them | There is a very high-level familiarity with the existence of online privacy rules, laws, and regulations Very rarely, people knew the details of these laws and regulations |
| Online companies being transparent with regards to personal information withheld Yes: 5 people - 25% No: 8 people - 40% Don't Know what to look for: 7 people - 35% | Companies are not transparent with people's personal data withheld or shared online. There is also a significant amount of people who are not properly informed enough to know what to look for |
| Open coding | Axial coding (Core findings) |
Companies need to communicate to gain client trust
| People want companies to be more transparent and have user-friendly disclosure agreements and interactions with their users |
Actions to keep online identity secure
| There seems to be a different level of awareness between the participants on what to do to keep their online identity more secure |
| Awareness of the availability of tools or training to keep digital identity more secure Yes: 75% No: 25% | For the most part, people are aware of the availability of tools to keep their identity more secure; very few knew all the options that are available for them to use and the difference between the utility of each tool |
| Had cybersecurity training Yes: 80% No: 20% | For the most part, people had some sort of cybersecurity awareness training, mainly due to their current or previous professions |
| Thoughts about training Helpful: 7 people - 35% Would like to be trained: 2 people - 10% Needs to be more user-centric and relevant: 9 people - 45% Does not care for it: 2 people - 10% | People thought that training is helpful but would like it to be more user-centric |
| Accounts & password management systems adoption Paper: 25% Electronic password manager or electronic manual system: 30% None: 45% | Low adoption of password management tools, due to the complexity of the tool or the distrust in the vendor due to lack of transparency |
| Ideal solution to keep identity more secure - Use websites in incognito mode: 1 person - 5% - Mask credit card information: 1 person - 5% - Don't know what to look for: 6 people - 5% - A tool to provide more transparency and control: 7 people - 35% - Digital Identity management tool (Keep track of passwords and websites): 6 people - 30% - A tool to provide what digital identity information out on the internet: 7 people - 35% - A tool to notify if anyone unauthorized used their digital identity: 7 people - 35% - Universal username and password with some way of authentication - A tool to eliminate complexity in accessing online accounts | Various ideas about solutions emerged, most of the responses geared towards more transparency and more control of their Digital Identity |
| Unmet needs to keep digital identity more secure - More transparency & control: 6 people - 30% - No, or Don't know what to look for: 8 people - 40% - Would like training and information about options: 6 people - 30% | People wanted more transparency and control over their online digital data. They want training and awareness about the options available and what to look for in keeping their digital identity more secure |
Table 4. Axial Coding to Themes.
| Axial coding | Themes |
| Most people 55 to 75 are active online | Qualifier to the study: high internet adoption & use of digital identity - Predominantly high internet usage, with over 20+ online accounts making people 55 to 75 a ripe target for cyberattacks and digital identity compromises - Knowledgeable of what their digital identity entails |
| Most of the people didn't readily know all of the online accounts they used in the last 5 to 10 years | |
Acknowledged that their digital identity encompasses online personal data as well as online interactions, associations, and behavior | |
| Accept the risk as it is part of life right now, especially when the convenience outweighs the risks | 1) People accept the risk when it affects their convenience People are aware of some of the risks due to first-hand or second-hand exposure |
| Most people have been or know someone who has been affected by an online data breach | |
| People's online behavior was not affected by experiencing or knowing about cybersecurity breaches | |
| Risks about online presence and reputation being compromised mattered to individuals who are socially active, influential or their jobs get affected by a digital identity compromise | |
| Risks about online banking and financial losses mattered to people who have been directly or indirectly affected by a compromise. People seem to trust their financial institutions to protect them and their money | |
| Digital identity compromises and cybersecurity risks are not a deterrent for people fully using the internet to their needs | |
| In very rare occasions, companies are providing details about online data breaches | 2) People are concerned that companies are not being transparent with regards to being good custodians of their digital identity |
| There is a very high-level familiarity with the existence of online privacy rules, laws, and regulations. Very rarely people knew the details of these laws and regulations |
Table 4 (Continued)
| Axial coding | Themes |
| Companies are not transparent with people's personal data withheld or shared online. There is also a significant amount of people who are not properly informed enough to know what to look for | 2) People are concerned that companies are not being transparent with regards to being good custodians of their digital identity |
| People want companies to be more transparent and have user-friendly disclosure agreements and interactions with their users | |
| There seems to be a different level of awareness between the participants on what to do to keep their online identity more secure | 3) People are aware of the availability of tools and trainings to help manage the risks. But they need more awareness education about their options and the utility of the tools and the training to use them properly while making an informed decision and staying user centric |
| For the most part, people are aware of the availability of tools to keep their identity more secure; very few knew all the options available for them to use and the difference between the utility of each tool | |
| For the most part, people had some sort of cybersecurity awareness training, mainly due to their current or previous professions | |
| People thought that training is helpful but would like it to be more user-centric | |
| Low adoption of password management tools, due to the complexity of the tool or the distrust in the vendor due to lack of transparency | |
| Various ideas about solutions emerged, most of the responses geared towards more transparency and more control of their digital identity | 4) People want more transparency and control over their digital identity to help them ease their concerns of the risks |
| People wanted more transparency and control over their online digital data. They want training and awareness about the options available and what to look for in keeping their digital identity more secure |
Table of Contents
- CHAPTER ONE - INTRODUCTION
- CHAPTER TWO - ABOUT IDENTITY
- CHAPTER THREE - LITERATURE REVIEW
- CHAPTER FOUR - METHODOLOGY
- CHAPTER FIVE - FINDINGS
- CHAPTER SIX - DISCUSSION
- REFERENCES
- APPENDIX A - INTERVIEW SOLICITATION FLYER
- APPENDIX B - IRB VERBAL CONSENT FORM
- APPENDIX C - INTERVIEW QUESTIONNAIRE
- APPENDIX D - IRB APPROVAL EXEMPT FORM
- APPENDIX E - ITRC 2019 DATA BREACH REPORT STATISTICS